劳动模范黑客挑战劳动模范雷军:我就是你最糟糕的公关噩梦
【摘要】:51可以说是雷军的节日,因为很多人都说雷军就是劳动模范,不过,一个黑客哥们可能也是劳动模范,这次,劳动模范雷军可能碰到了一个棘手的劳动模范黑客的挑战问题。
福布斯在劳动节发了一篇著名黑客的调查,表示小米智能手机大规模侵犯个人隐私,即使在匿名无痕浏览状态之下也会上传你的浏览记录包括一些色情网站等的个人隐私信息,而且传播的时候是带着你的手机的特点信息的。
然后小米通过博客作了公开回应,认为黑客哥们的的说法是不真实错误的,黑客可能没弄清楚小米的隐私政策。
不过,凌通社去看了一下黑客哥们的推,发现这黑客是来者不善,劳动节也不休息,专门录制了一段小米传输记录的视频,并且表示,我就是你最糟糕的公关噩梦。因为这个事情是昨天开始的,凌通社这次的内容用倒叙的方式写,如果你不清楚可以查一下背景或者从后面开始阅读。
雷军对手:黑客哥们来者不善

黑客称:您先看最新视频
黑客哥们战绩:破解最安全的钱包
黑客挑战:我就是你最糟糕的公关噩梦
黑客4分钟演示小米手机传输
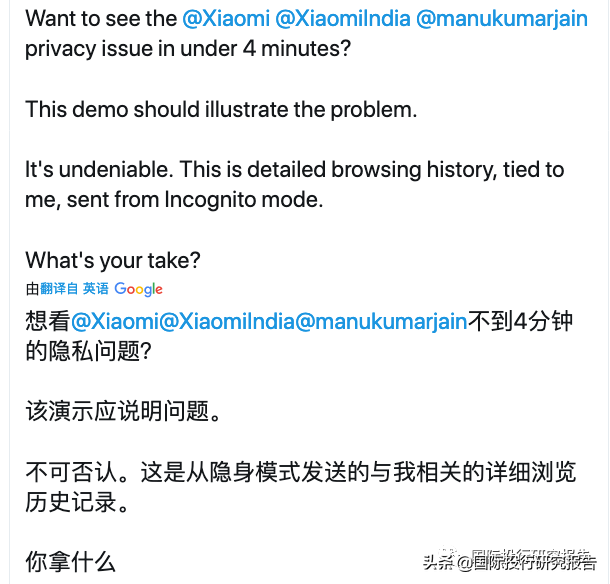
黑客称:其他浏览器通过编码传输
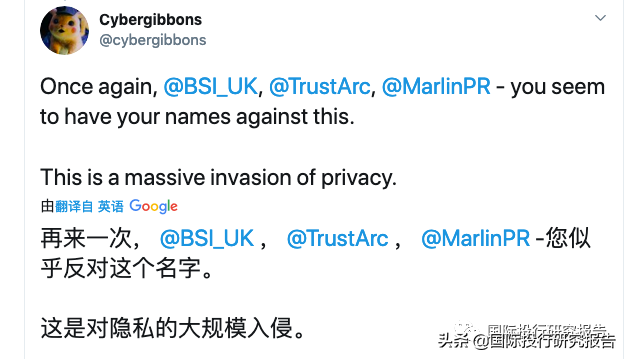
小米印度发布的声明:不正确
南华早报:研究者称
小米手机发送搜索和浏览数据回中国
福布斯独家:警报!中国移动巨头小米记录数百万人民的”个人”网络和电话记录


“It’s a backdoor with phone functionality,” quips Gabi Cirlig about his new Xiaomi phone. He’s only half-joking.
Cirlig is speaking with Forbes after discovering that his Redmi Note 8 smartphone was watching much of what he was doing on the phone. That data was then being sent to remote servers hosted by another Chinese tech giant, Alibaba, which were ostensibly rented by Xiaomi.
The seasoned cybersecurity researcher found a worrying amount of his behavior was being tracked, whilst various kinds of device data were also being harvested, leaving Cirlig spooked that his identity and his private life was being exposed to the Chinese company.
“这是具有电话功能的后门,”加比·西里格(Gabi Cirlig)嘲笑他的新小米手机。他只是在开玩笑。
Cirlig发现自己的Redmi Note 8智能手机正在注视着他在手机上所做的许多事情后,便与《福布斯》进行了交谈。然后,这些数据被发送到另一家中国科技巨头阿里巴巴托管的远程服务器上,这些服务器表面上是小米租用的。
这位经验丰富的网络安全研究员发现,他的行为令人担忧,同时还收集了各种设备数据,这使Cirlig感到惊恐,因为他的身份和私生活正暴露给这家中国公司。
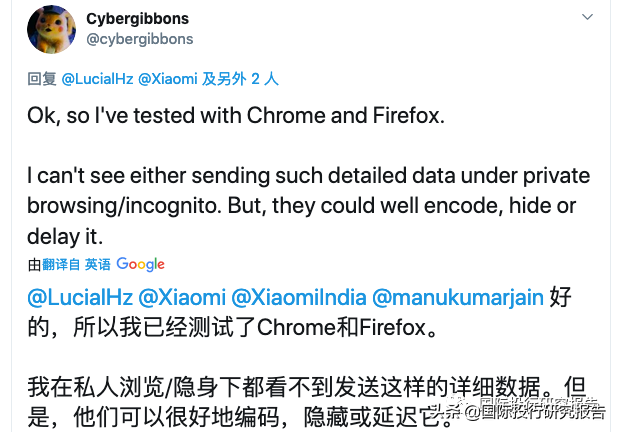
When he looked around the Web on the device’s default Xiaomi browser, it recorded all the websites he visited, including search engine queries whether with Google or the privacy-focused DuckDuckGo, and every item viewed on a news feed feature of the Xiaomi software. That tracking appeared to be happening even if he used the supposedly private “incognito” mode.
The device was also recording what folders he opened and to which screens he swiped, including the status bar and the settings page. All of the data was being packaged up and sent to remote servers in Singapore and Russia, though the Web domains they hosted were registered in Beijing.
当他在设备的默认小米浏览器上浏览网络时,它记录了他访问过的所有网站,包括使用Google或专注于隐私的DuckDuckGo进行的搜索引擎查询,以及在小米软件的新闻提要功能上查看的每个项目。即使他使用了所谓的私有“隐身”模式,该跟踪似乎仍在发生。
该设备还记录了他打开了哪些文件夹以及向哪个屏幕滑动,包括状态栏和设置页面。所有数据都被打包并发送到新加坡和俄罗斯的远程服务器,尽管它们托管的Web域在北京注册。
Meanwhile, at Forbes’ request, cybersecurity researcher Andrew Tierney investigated further. He also found browsers shipped by Xiaomi on Google Play—Mi Browser Pro and the Mint Browser—were collecting the same data. Together, they have more than 15 million downloads, according to Google Play statistics.
Many more millions are likely to be affected by what Cirlig described as a serious privacy issue, though Xiaomi denied there was a problem. Valued at $50 billion, Xiaomi is one of the top four smartphone makers in the world by market share, behind Apple, Samsung and Huawei. Xiaomi’s big sell is cheap devices that have many of the same qualities as higher-end smartphones. But for customers, that low cost could come with a hefty price: their privacy.
同时,应福布斯的要求,网络安全研究员安德鲁·蒂尔尼(Andrew Tierney)进行了进一步调查。他还发现小米在Google Play上发布的浏览器(Mi Browser Pro和Mint Browser)正在收集相同的数据。根据Google Play的统计,它们的下载量总计超过1500万。
尽管小米否认存在问题,但还有更多的人可能会受到Cirlig所说的严重的隐私问题的影响。小米的市值达500亿美元,是全球市场前四大智能手机制造商之一,仅次于苹果,三星和华为。小米最大的卖点是便宜的设备,它们具有与高端智能手机相同的质量。但是对于客户而言,这种低成本可能会带来高昂的价格:他们的隐私。
Cirlig thinks that the problems affect many more models than the one he tested. He downloaded firmware for other Xiaomi phones—including the Xiaomi MI 10, Xiaomi Redmi K20 and Xiaomi Mi MIX 3 devices. He then confirmed they had the same browser code, leading him to suspect they had the same privacy issues.
And there appear to be issues with how Xiaomi is transferring the data to its servers. Though the Chinese company claimed the data was being encrypted when transferred in an attempt to protect user privacy, Cirlig found he was able to quickly see just what was being taken from his device by decoding a chunk of information that was hidden with a form of easily crackable encoding, known as base64. It took Cirlig just a few seconds to change the garbled data into readable chunks of information.
“My main concern for privacy is that the data sent to their servers can be very easily correlated with a specific user,” warned Cirlig.
Cirlig认为,问题所影响的型号比他所测试的型号还要多。它下载了其他小米手机的固件,包括小米MI 10,小米Redmi K20和小米MIX 3设备。然后,他确认它们具有相同的浏览器代码,从而使他怀疑它们具有相同的隐私问题。
小米将数据传输到其服务器的方式似乎存在问题。尽管这家中国公司声称为了保护用户隐私而对数据进行了加密,但Cirlig发现,他可以通过解码大量信息(通过一种很容易隐藏的形式)来快速查看从设备中窃取的内容。易破解的编码,称为base64。Cirlig只花了几秒钟的时间就将乱码的数据变成了可读的信息块。
“我对隐私的主要关注是发送到其服务器的数据可以很容易地与特定用户相关联,” Cirlig警告说。
Xiaomi’s response
小米的回复
In response to the findings, Xiaomi said, “The research claims are untrue,” and “Privacy and security is of top concern,” adding that it “strictly follows and is fully compliant with local laws and regulations on user data privacy matters.” But a spokesperson confirmed it was collecting browsing data, claiming the information was anonymized so wasn’t tied to any identity. They said that users had consented to such tracking.
But, as pointed out by Cirlig and Tierney, it wasn’t just the website or Web search that was sent to the server. Xiaomi was also collecting data about the phone, including unique numbers for identifying the specific device and Android version. Cirlig said such “metadata” could “easily be correlated with an actual human behind the screen.”
Xiaomi’s spokesperson also denied that browsing data was being recorded under incognito mode. Both Cirlig and Tierney, however, found in their independent tests that their web habits were sent off to remote servers regardless of what mode the browser was set to, providing both photos and videos as proof.
When Forbes provided Xiaomi with a video made by Cirlig showing how his Google search for “porn” and a visit to the site PornHub were sent to remote servers, even when in incognito mode, the company spokesperson continued to deny that the information was being recorded. “This video shows the collection of anonymous browsing data, which is one of the most common solutions adopted by internet companies to improve the overall browser product experience through analyzing non-personally identifiable information,” they added.
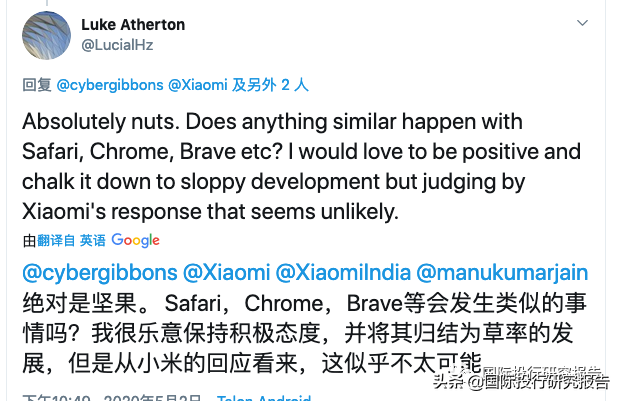
Both Cirlig and Tierney said Xiaomi’s behavior was more invasive than other browsers like Google Chrome or Apple Safari. “It’s a lot worse than any of the mainstream browsers I have seen,” Tierney said. “Many of them take analytics, but it's about usage and crashing. Taking browser behavior, including URLs, without explicit consent and in private browsing mode, is about as bad as it gets.”
Cirlig also suspected that his app use was being monitored by Xiaomi, as every time he opened an app, a chunk of information would be sent to a remote server. Another researcher who’d tested Xiaomi devices, though was under an NDA to discuss the matter openly, said he’d seen the manufacturer’s phone collect such data. Xiaomi didn’t respond to questions on that issue.
小米在回应调查结果时说:“研究声称是不真实的,而隐私和安全是头等大事。”他补充说,“严格遵守并完全遵守有关用户数据隐私问题的当地法律法规。”但是一位发言人证实,它正在收集浏览数据,声称该信息是匿名的,因此与任何身份无关。他们说用户已经同意这种跟踪。
但是,正如Cirlig和Tierney所指出的那样,发送到服务器的不仅仅是网站或网络搜索。小米还收集有关手机的数据,包括用于识别特定设备和Android版本的唯一编号。Cirlig说,这样的“元数据”可以“很容易地与屏幕后面的实际人相关联。”
小米发言人还否认浏览数据是在隐身模式下记录的。但是,Cirlig和Tierney均在独立测试中发现,无论浏览器设置为哪种模式,他们的网络习惯都会发送到远程服务器,同时提供照片和视频作为证明。
当福布斯向小米提供由Cirlig制作的视频时,即使是在隐身模式下,该视频也显示了他的Google搜索“色情”内容和对PornHub网站的访问是如何发送到远程服务器的,该公司发言人继续否认信息被记录。他们补充说:“该视频显示了匿名浏览数据的收集,这是互联网公司通过分析非个人可识别信息来改善整体浏览器产品体验的最常见解决方案之一。”
Cirlig和Tierney都说,小米的行为比其他浏览器(例如Google Chrome或Apple Safari)更具侵略性。Tierney说:“这比我见过的任何主流浏览器都差很多。” “他们中的许多人都接受分析,但这与使用和崩溃有关。未经明确同意并以私密浏览模式进行浏览器行为(包括URL),就和它一样糟糕。”
Cirlig还怀疑小米会监视他的应用程序使用,因为每次打开某个应用程序时,大量信息都会发送到远程服务器。另一位曾测试过小米设备的研究人员尽管处于保密协议之下,正在公开讨论此事,但他表示,他已经看到制造商的电话正在收集此类数据。小米未回答有关该问题的问题。
‘Behavioral Analytics’
行为分析
Xiaomi appears to have another reason for collecting the data: to better understand its users’ behavior. It’s using the services of a behavioral analytics company called Sensors Analytics. The Chinese startup, also known as Sensors Data, has raised $60 million since its founding in 2015, most recently taking $44 million in a round led by New York private equity firm Warburg Pincus, which also featured funding from Sequoia Capital China. As described in Pitchbook, a tracker of company funding, Sensors Analytics is a “provider of an in-depth user behavior analysis platform and professional consulting services.” Its tools help its clients in “exploring the hidden stories behind the indicators in exploring the key behaviors of different businesses.”
Both Cirlig and Tierney found their Xiaomi apps were sending data to domains that appeared to reference Sensors Analytics, including the repeated use of SA. When clicking on one of the domains, the page contained one sentence: “Sensors Analytics is ready to receive your data!” There was an API called SensorDataAPI—an API (application programming interface) being the software that allows third parties access to app data. Xiaomi is also listed as a customer on Sensors Data’s website.
The founder and CEO of Sensors Data, Sang Wenfeng, has a long history in tracking users. At Chinese internet giant Baidu he built a big data platform for Baidu user logs, according to his company bio.
Xiaomi’s spokesperson confirmed the relationship with the startup: “While Sensors Analytics provides a data analysis solution for Xiaomi, the collected anonymous data are stored on Xiaomi's own servers and will not be shared with Sensors Analytics, or any other third-party companies.”
It’s the second time in two months that a huge Chinese tech company has been seen watching over users’ phone habits. A security app with a “private” browser made by Cheetah Mobile, a public company listed on the New York Stock Exchange, was seen collecting information on Web use, Wi-Fi access point names and more granular data like how a user scrolled on visited Web pages. Cheetah argued it needed to collect the information to protect users and improve their experience.
Late in his research, Cirlig also discovered that Xiaomi’s music player app on his phone was collecting information on his listening habits: what songs were played and when.
One message was clear to the researcher: when you’re listening, Xiaomi is listening, too.
小米似乎还有另一个收集数据的理由:更好地了解其用户的行为。它使用的是行为分析公司Sensors Analytics的服务。自2015年成立以来,这家中国初创公司又被称为Sensors Data,已经筹集了6000万美元,最近在纽约私募股权公司Warburg Pincus领投的一轮融资中获得了4400万美元,该轮融资还来自红杉资本中国。正如公司资金追踪器Pitchbook所述,Sensors Analytics是“深入的用户行为分析平台和专业咨询服务的提供者”。它的工具可帮助客户“探索指标背后的隐藏故事,以探索不同业务的关键行为。”
Cirlig和Tierney都发现他们的Xiaomi应用程序正在将数据发送到似乎引用Sensors Analytics的域,包括重复使用SA。单击其中一个域时,页面包含一句话:“ Sensors Analytics已准备就绪,可以接收您的数据!”有一个称为SensorDataAPI的API-一种API(应用程序编程接口),它是允许第三方访问应用程序数据的软件。小米在Sensors Data的网站上也被列为客户。
Sensors Data的创始人兼首席执行官桑文峰在追踪用户方面拥有悠久的历史。据他的公司介绍,在中国互联网巨头百度,他为百度用户日志构建了一个大数据平台。
小米的发言人证实了与这家初创公司的关系:“虽然Sensors Analytics为小米提供了数据分析解决方案,但收集的匿名数据存储在小米自己的服务器上,不会与Sensors Analytics或任何其他第三方公司共享。”
这是两个月来第二次看到一家大型中国科技公司关注用户的电话习惯。在纽约证券交易所上市的Cheetah Mobile(一家上市公司)开发的一款带有“私有”浏览器的安全应用被发现收集了有关Web使用,Wi-Fi接入点名称以及更细粒度的数据(如用户如何滚动访问)的信息。网页。猎豹认为,它需要收集信息以保护用户并改善他们的体验。
在研究的后期,Cirlig还发现小米手机上的音乐播放器应用正在收集有关他的收听习惯的信息:播放什么歌曲以及何时播放。
研究人员清楚地传达了一条信息:当您在听时,小米也在听。
UPDATE: Xiaomi posted a blog in which it delineated how and when it collects visited URLs visited by its users. Read it in full here.
The company reiterated that the data transferred from Xiaomi devices and browsers was anonymized and not attached to any identity.
更新:小米发布了一个博客,其中描述了如何以及何时收集其用户访问的访问URL。在这里完整阅读。
该公司重申,从小米设备和浏览器传输的数据是匿名的,没有附加任何身份。
小米博客回复全文
小米公司希望其用户在这段困难时期保持安全。昨天发表了一篇关于小米隐私政策的文章,其中对我们的浏览器数据收集和存储流程存在几个不准确和误解。我们在下面的备份文档中提供支持我们立场的重要说明:
小米评论了《福布斯》最近一篇关于我们隐私政策的文章,并认为这篇报道歪曲了事实。在小米,我们用户的隐私和安全是重中之重。我们严格遵守并完全遵守我们运营的国家和地区的用户隐私保护法律法规。鉴于这些事实陈述,我们想澄清以下几点:
1.在所有小米正式入驻的全球市场,为了提供尽可能好的用户体验,增加操作系统与各种应用之间的兼容性,并承担保护用户隐私的义务,所有收集的使用数据都是基于我们用户明确许可和同意的。此外,我们还确保整个过程是匿名和加密的。汇总使用统计数据的收集用于内部分析,我们不会将任何个人身份信息与这些数据中的任何数据相关联。此外,这是世界各地的互联网公司普遍采用的解决方案,以改善各种产品的整体用户体验,同时保护用户隐私和数据安全。
2.小米在公有云基础设施上托管信息,该公有云基础设施是行业内常见和知名的。我们海外服务和用户的所有信息都存储在各个海外市场的服务器上,这些市场严格遵守当地用户隐私保护法律和法规,我们也完全遵守这些法律和法规。
3.上述文章发表前,记者给我们发了邮件,提出了与文章相关的问题,小米以完全透明的方式做出回应,就我们的技术和隐私政策提供了详细的解答。我们认为发表的文章没有准确反映这些通信的内容和事实。在文章发布后,我们联系了记者,进一步澄清了这一点,目前正在讨论中,目的是迅速向他们保证我们的数据安全流程是如何运作的。
4.作为一家互联网公司,网络安全和用户隐私是小米遵守的核心原则,也是我们日常工作的基础。我们在用户隐私保护方面的产品、技术、性能和措施都在不断完善。在我们最新推出的操作系统MIUI 12中,我们采用了迄今为止业界最严格和最透明的隐私保护措施。为了增加透明度,我们始终欢迎公众以事实为基础的监督、询问和讨论,以不断改进我们为亲爱的用户和米粉提供的产品和服务。
印度媒体对小米回复的报道
小米在声称网络数据被记录后感到“误解”

为了遏制小米昨天被控记录浏览数据还有电话习惯的的喧嚣,这家中国科技巨头发了一个博客帖子为其数据实践辩护。
此前,网络安全研究人员Cirlig告诉福布斯他的Redmi Note 8上的每一次触摸都被记录下来并发送到远程服务器。这包括打开哪个文件夹、哪个屏幕被滑动、播放哪首歌等等。
Cirlig最担心的是被记录在小米默认浏览器和薄荷浏览器上的浏览数据。这位研究人员称,小米正在录制谷歌的查询、访问的网站、以及在新闻上浏览的内容。
Cirlig在一段视频中证明,即使在隐匿模式下,私人数据的记录也不会停止。他还证实了小米其他智能手机也采用了同样的做法。
在这篇博文中,小米声称收集到的数据被汇总并用于内部分析。此外,所有内容都是用户同意的,并且是基于权限的。
这是世界各地的互联网公司为提高各种产品的整体用户体验而采取的共同解决方案,同时也保护了用户的隐私和数据安全。
小米写道,聚合使用统计数据,如系统信息、用户界面功能使用、响应性和性能,不能用于识别单个用户。它还说,只有当功能打开时,浏览数据才是“同步的”。
至于小米默认浏览器中的匿名模式,该公司否认了该研究人员关于数据收集的说法,但它写道,汇总使用统计数据仍在收集之中。此外,小米仅部分否认了网络数据以匿名方式录制的视频证据。它说,视频显示收集“匿名浏览数据”。
有趣的是,这篇博文并没有包含小米发言人没有告诉“福布斯”的任何内容。虽然收集到的数据是汇总的,但Cirlig告诉小米的手机数据中包含了识别特定设备的唯一号码。这与从浏览器中获取的数据“很容易与屏幕后面的实际人员相关联”。






















评论